Authelia + LLDAP + Traefik ForwardAuth Setup guide
This quick guide should take you through the steps necessary to setup Authelia as your forwardAuth for Traefik. We’ll be using LLDAP as the backend for Authelia since it’s lightweight and simple enough for most users. A more complete video is available on our YouTube Channel.
Prerequisites
- Traefik installed (enable the
premium train) - Clusterissuer for certificates
- CloudnativePG operator (enable the
system train)
Setup LLDAP
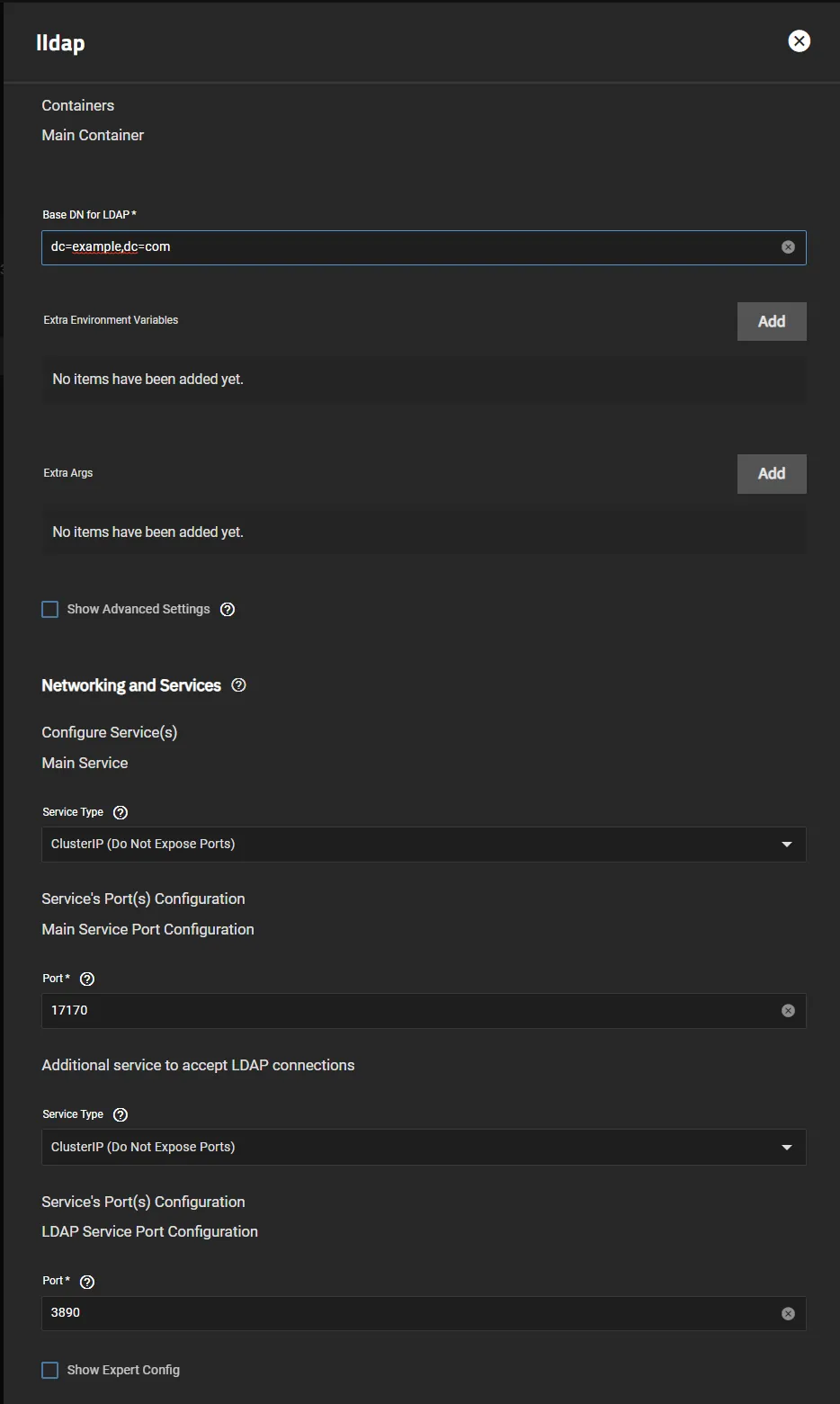
- Follow the easy steps included in the Installation Notes for LLDAP. Change
dc=example,dc=comto your domain, i.e.dc=MYDOMAIN,dc=netand then change your password. Also, make sure you have thesystemtrain enabled andCloudnativePGoperator installed, since you’ll need it forLLDAPandAuthelia.
-
Ensure you’ve set the services to
ClusterIPsince you’ll be using ingress -
Once in
LLDAP, create a user inside thelldap_password_managergroup and change your defaultadminpassword. Thatlldap_password_manageruser will be used to bind toAuthelia. Here I’ve created a user calledSteven, but you can use anything -
Create an
admingroup and addStevento it. We will allow users of this group to access the site with Authelia later in the guide.
Setup Authelia
- The setup for Authelia is very specific and the logs won’t tell you where you’ve messed up, but there’s precise steps used to integrate
LLDAPintoAuthelia. The info comes from the LLDAP Authelia Docs and the upstream repo.
App Configuration
- Domain:
mydomain.com- Your domain without https:// - Default Redirection URL:
https://auth.mydomain.com- Can be anything, but we’ll stick to auth.mydomain.com. As well, this will be the ingress URL forAuthelia.
LDAP Backend Configuration
Click Enable then ensure everything is as below or you won’t be able to connect to the LLDAP backend:
- Implementation:
Custom(that’s the default) - URL:
ldap://lldap-ldap.ix-lldap.svc.cluster.local:3890 - Connection Timeout: 5s
- Start TLS: (Not necessary)
- TLS Settings: (Not necessary)
- Server Name: Leave blank
- Skip Certificate Verification: Leave unchecked
- Minimum TLS version:
TLS1.2 - Base DN:
DC=mydomain,DC=com - Username Attribute:
uid - Additional Users DN:
ou=people - Users Filter:
(&(|({username_attribute}={input})({mail_attribute}={input}))(objectClass=person)) - Additional Groups DN:
ou=groups - Groups Filter:
(member={dn}) - Group name Attribute:
cn - Mail Attribute:
mail - Display Name Attribute:
displayName - Admin User:
uid=Steven,ou=people,dc=mydomain,dc=com- Notice the uid=Steven, most of the time people use admin and a generated password - Password:
RANDOMPASSWORD
SMTP Configuration
Check your mail provider for this, generally Gmail gives you an app specific password for your email account and uses smtp.gmail.com and port 587.
Access Control Configuration
This section is to set rules to connect to Authelia and defines which users can go where. This is a basic general rule where users of the admin group (Steven) can access all of the site using a wildcard.
Set the default deny. Then click Add next to Rules to get the screen below.
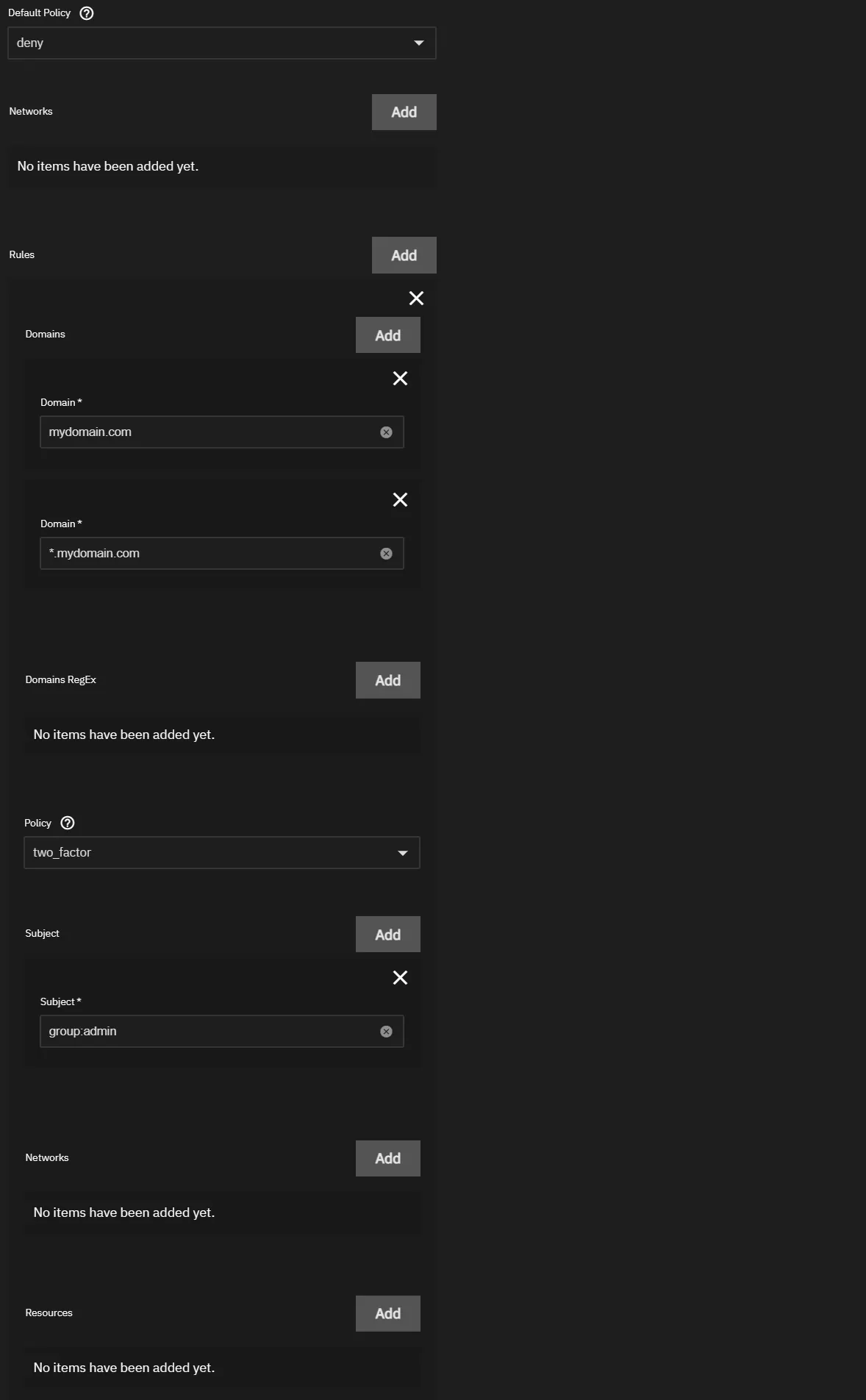
- Add your
Domainand aWildcardfor your subdomains - Set policy to
one_factorortwo_factor, up to you - Click
Add Subjectand add a subject ofgroup:adminsinceStevenis part of that group.
Please see Authelia Rules for more advanced rules.
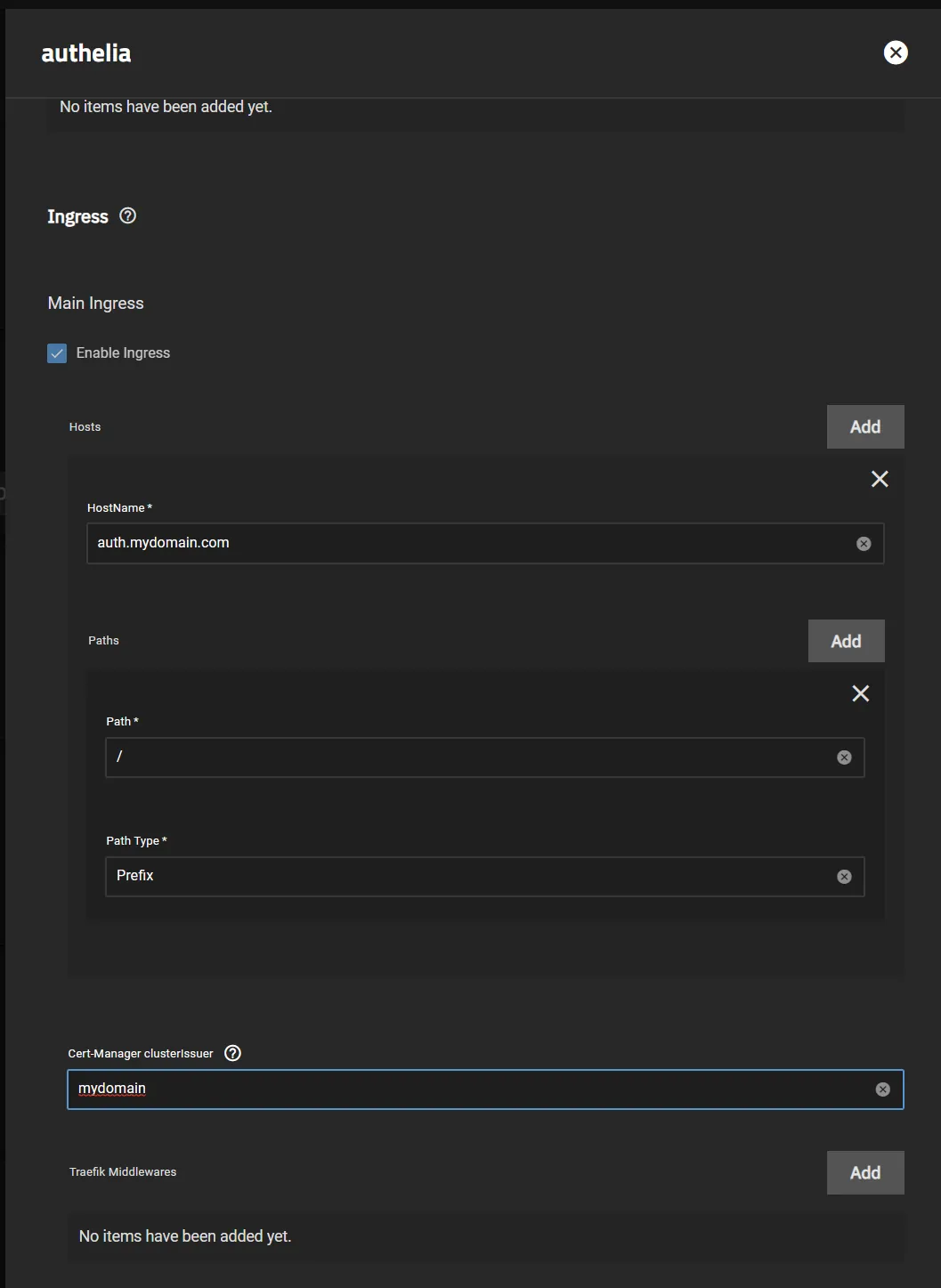
Setup Authelia Ingress
- Make sure you’re using the same domain as the
Default Redirection URLabove, so for me that’sauth.mydomain.com
Traefik ForwardAuth Setup
-
This part is straight forward as long as you have a working
Traefikinstall, please see our How-To if you need more info on getting that running. -
Scroll down to
forwardAuthand clickAdd
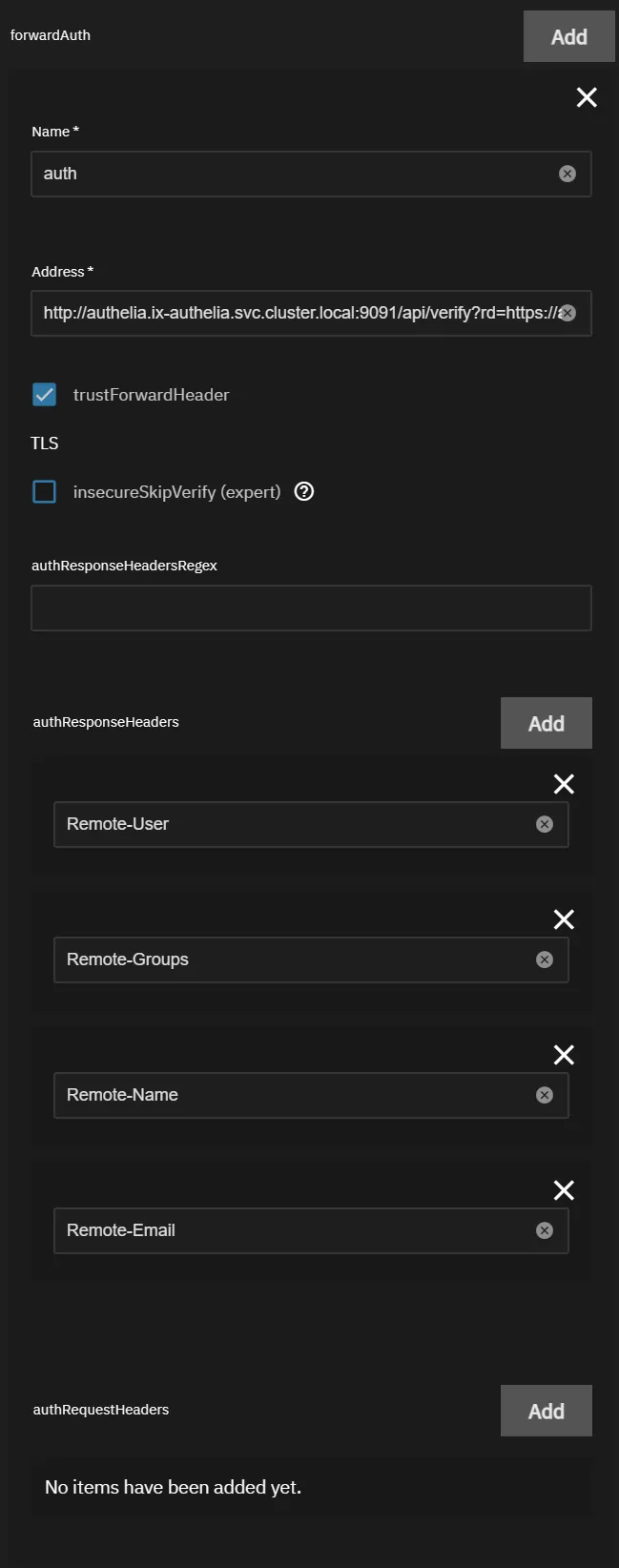
- Name your
forwardauthsomething you’ll remember, since that’s the middleware you’ll add to your ingress going forward. Most people useauth - Address:
http://authelia.ix-authelia.svc.cluster.local:9091/api/verify?rd=https://auth.mydomain.com/and replace the last part based onmydomain.com, and if you’ve changed ports/names you can get that fromHeavyScript - Check
trustForwardHeader - Add the following
authResponseHeaders(pressAdd4 times)Remote-UserRemote-GroupsRemote-NameRemote-Email
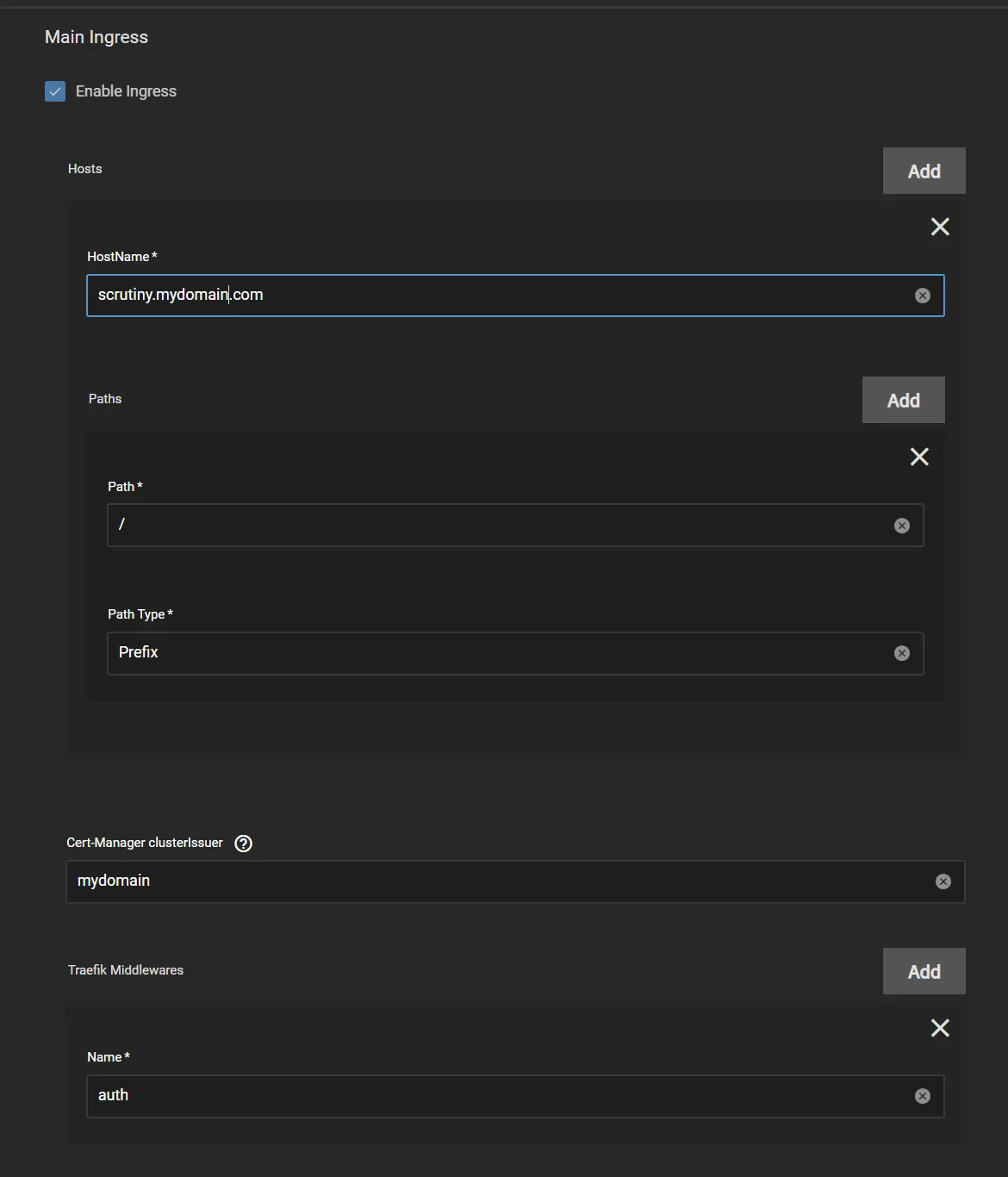
Adding the forwardauth to your Apps
The last step is adding the forwardauth along with the standard ingress settings for your app, for more info on setting ingress see the ClusterIssuer Guide. What changes versus a standard setup is the Traefik Middlewares section, where you must add your forwardauth to the section.
- In this example we use the same name as above, or
auth. ClickAddto theTraefik Middlewaressection, and enter yourforwardauthname.
References
The origin material for this guide is available on the LLDAP Github. While further information on Authelia can be found on their Github and website.
Support
If you have any issues with following this guide, we can be reached using Discord for real-time feedback and support.